03.03.2021
Scientists of ETU "LETI" Youth Research Institute and the Aristotle University of Thessaloniki developed a new algorithm for constructing hash functions based on chaos theory.
Researchers of ETU "LETI" and Aristotle University of Thessaloniki have created a new algorithm for constructing hash functions. Taking advantage of chaos theory and adaptive symmetry, the scientists made it harder to break than existing solutions. The results of the study are published in the Chaos, Solitons & Fractals journal.
A hash function is a mathematical function designed to convert some message or data, such as a password, into a bit array called a hash. This way, the system processes code that is unique to each message. It is essentially a way to verify encoded messages, impossible to decrypt unambiguously. For example, when we enter a password in a system that uses hash functions, the server receives not the text of our password itself but its bit array. If it matches the sequence on the server, then we log in to our account. The point is that if intruders intercept our message, they won't get the plain text of our password but the bit array, which they won't be able to decrypt correctly.
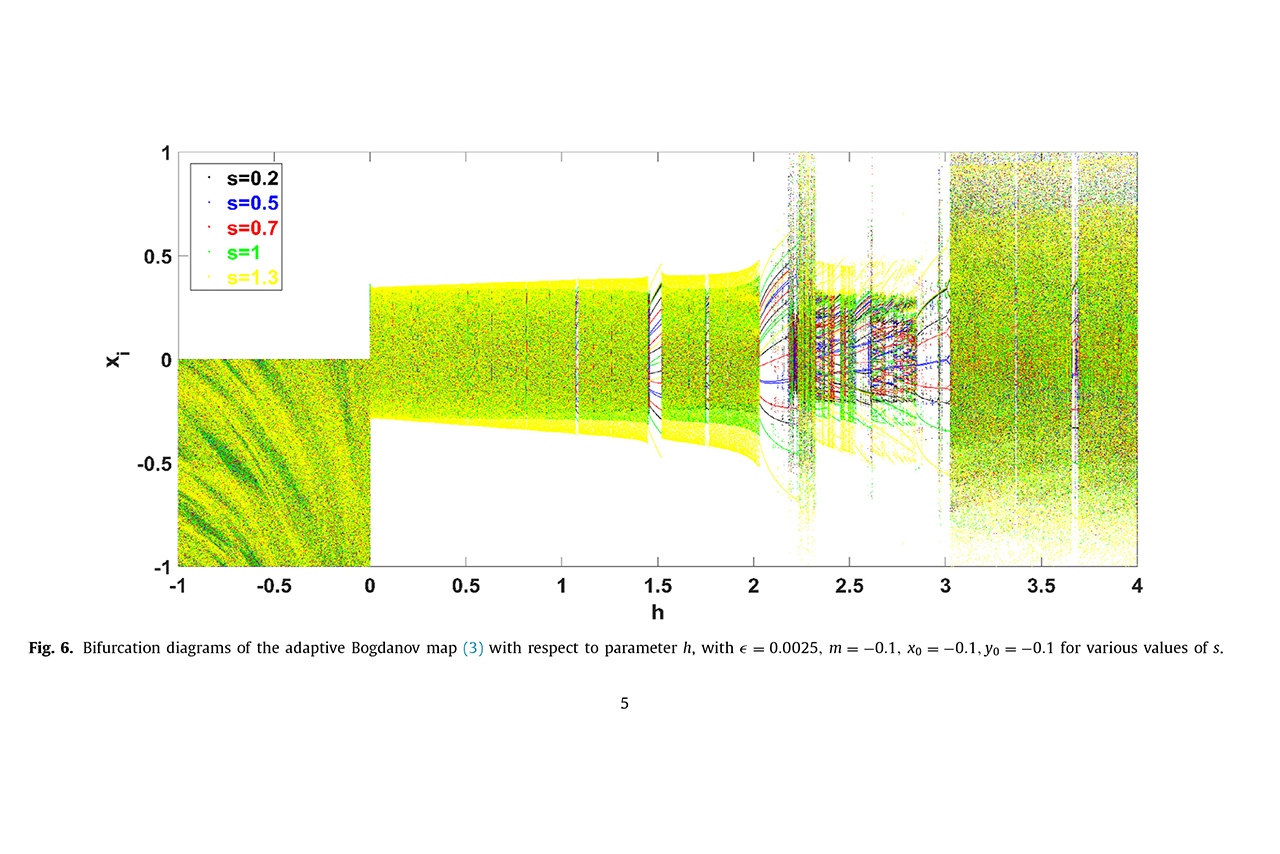
Hash functions are used in many areas: data encryption, electronic signatures, cryptocurrencies, data sorting and compression. In modern cryptography, one of the most promising areas is chaotic hash functions based on chaos theory. This theory describes the dynamics of nonlinear systems in which changes in initial conditions lead to unpredictable consequences. Such systems include mechanical devices like a double pendulum, atmospheric phenomena models, population dynamics, and even some social processes. But since we need as random a sequence of bits as possible for hashing data, the use of chaotic systems with confusion and diffusion property facilitates this process, enhancing data security. The researchers from ETU "LETI" studied existing chaotic hash functions and developed their improved version.
of Computer Aided Design Systems
"Unlike other solutions based on classical chaotic maps, we used modifications with adaptive symmetry. The use of discrete maps with controlled symmetry expands the key space and, consequently, the cryptographic strength of the obtained hash functions. The symmetry of the maps becomes an additional key in their construction while having little effect on the chaotic behavior of the system." – said Alexandra Tutueva, Junior Researcher at the Youth Research Institute, a Ph.D. student at the Department of Computer Aided Design Systems of ETU "LETI".
After constructing the hash function, scientists have tested it thoroughly. Like any other counterparts, it must have certain properties of cryptographic hash functions. First of all, the authors analyzed the performance - how quickly the input data (keys) is converted into a bit array and back. For comparison, they used the known standard SHA-3 (Keccak) hash function and several currently existing chaotic functions. The development of ETU "LETI" researchers showed a speed of 0.9 Gbit/s, comparable with analogs.
The function also successfully passed the birthday attack test. This method is used in cryptanalysis to break ciphers. It is based on the birthday paradox. For example, in a group of 23 people, the probability that two of them will have the same birthday is greater than the probability that each of these people will have unique birthdays. That seems counterintuitive, but the math shows otherwise. Using this paradox, attackers try to discover the same bit arrays for two different source messages. So scammers using hash functions can send one contract to sign with e-signature, but the victim will end up signing two contracts with different contents at once. However, the scientists have established that for the new function it is enough to generate messages of at least 128 bits in length to prevent the attack. This way, the probability of a bit array match is minimized.
The authors also confirmed the avalanche effect of the function. It means that changes in the original data lead to changes in hashes. The researchers created a text message and then ran it through a hash function, obtaining a specific bit array. They then changed the length and meaning of the original texts and hashed those messages. The result was completely different bit sequences, indicating that the function worked correctly.
The new chaotic hash function passed all the tests and showed its reliability and efficiency. According to scientists, it can be used in cryptography as a more secure version of data transmission. Also, the new function can be the basis for a mechanism that creates realistic models of objects of fractal structure in computer graphics and solid-state modeling - for example, for the generation of clouds and mountains, the surface of the sea, the tensions within solids, and much more.
Share:

 Русский
Русский 中文
中文 Español
Español Français
Français العربية
العربية